In parallel with the development of network technology, a series of malicious software has been derived. Ransomware is hackers to hijack users assets or resources and as a condition to extort a malware to the user. CryptXXX has a variety of very hot lately, the new version of CryptXXX has become more aggressive.
Currently there are no solutions
New CryptXXX Ransomware not only encrypt the destination user's computer and all the files on the network, users are also unable to use data backup to restore the files--this is one of the most important features of the new CryptXXX upgrade.
Kaspersky Lab security researchers have been struggling with CryptXXX: previous researchers had published a decryption tool, the victims don't need to pay a ransom to restore their own files if no decryption tools, victims need to pay at least $ 500 to decrypt the file. CryptXXX developer found after Kaspersky's move, also begin to adjust program code makes it harder to break into. Recently developers have released a new version of CryptXXX. Security SentinelOne this company mentioned in a blog post Monday, June 4-June 21, the new version has reached the total ransom 45228 dollars, of course, this does not include the income of the previous version.
When actually as early as May 21, CryptXXX developers of the malware code is updated to version 3.0. The purpose of this update is to prevent Kaspersky launch RannohDecryptor decryption program, free unlocking the encrypted files.
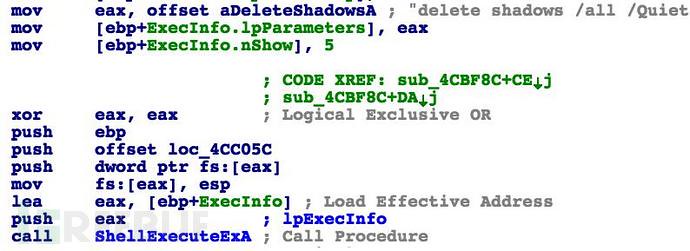
New version CryptXXX is still supported to encrypt a single file, but the file size limit in the 512KB. New versions of the main improvement is difficult to crack a lot. Other improvements included, than before. and crypz. crypt suffix, suffix version CryptXXX build encrypted files into the. crypt1; there is previously mentioned, delete shadow volume the volume of the system back up, prevent data can be restored from the backup. In addition, its communication is conducted through the spam, but SentinelOne said, hackers may also use other ways of communication.
Analysis of the new CryptXXX
View a malicious DLL file properties file properties details found it actually comes from a legitimate file called _BigBang.dll, details of both are essentially the same.
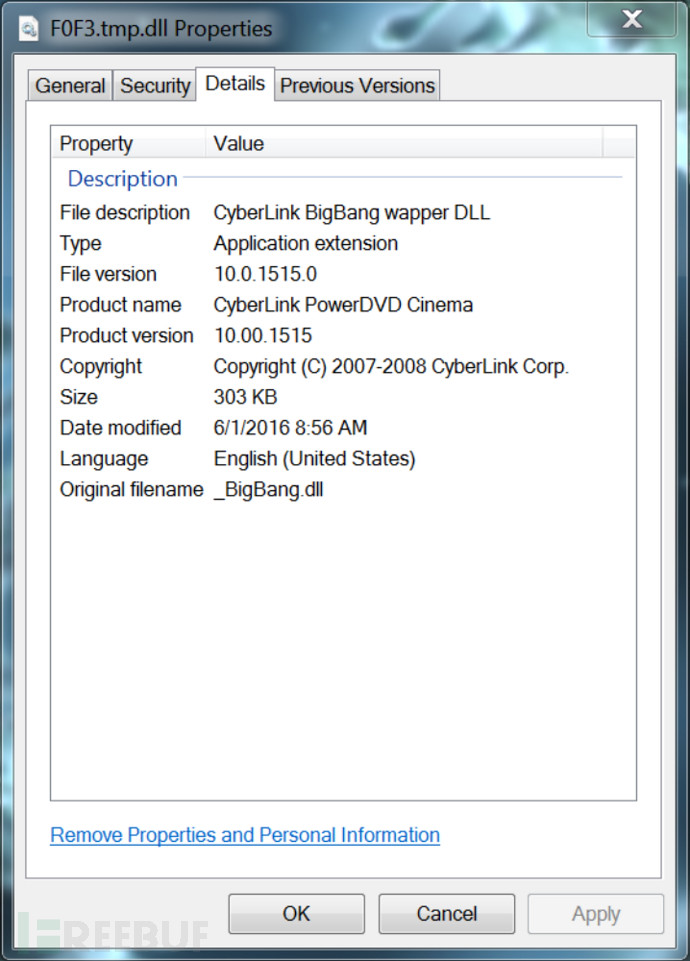
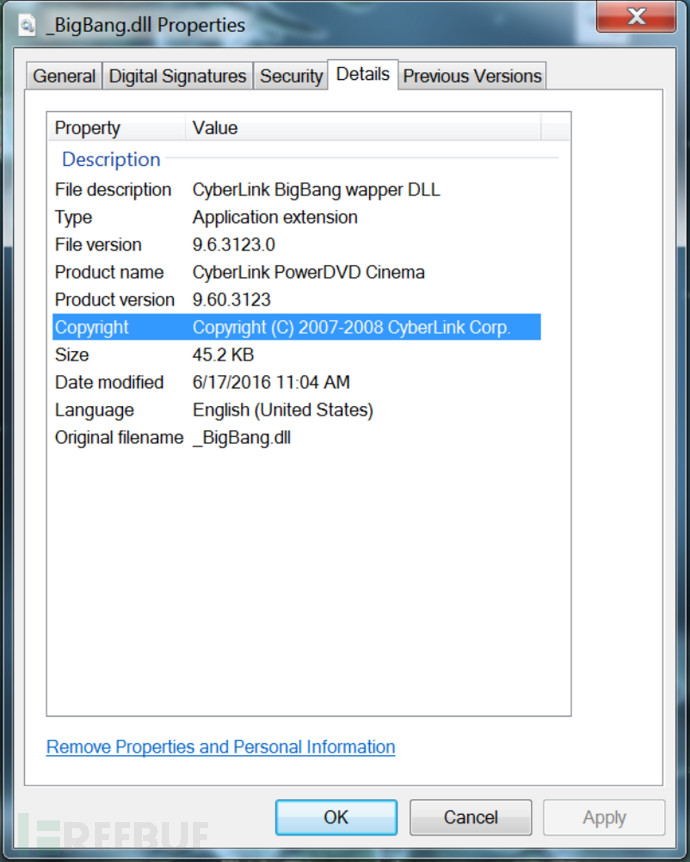
Details from the files, didn't see anything unusual, so that it looks just like a normal program. Previous CryptXXX samples will be disguised as legitimate DLL file from Microsoft. From unpacker imports, most of the content seems no problem, occasionally some vocabulary related to crypto encryption. Judging from list of imports and exports, many functions are related to image processing (and the above mentioned legal _BigBang.dll is certainly not the same), there seems to be no eggs used, these should be used to hinder analysis.
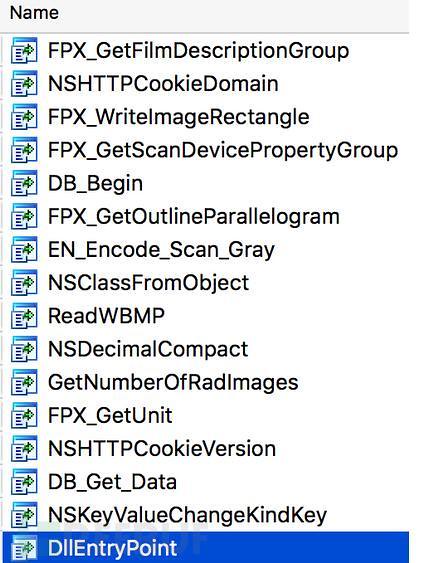
Unpack process is by VirtualAlloc allocates memory as an encrypted payload, and then copy the encrypted bytes. Then decrypt the payload, but it is still compressed.
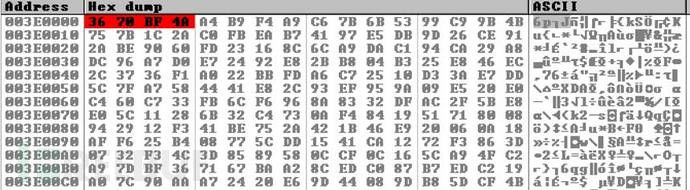
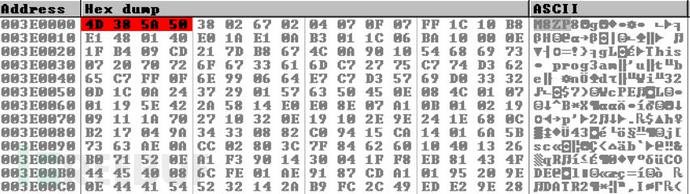
Based on the experience of a version where you can look for "MZ" header, but found the "M8ZP8" part and read the string "This? Progr3am ... ", but this is normal for Windows executable. M8ZP8 consistent with the aPLiB compression PE files.
Click here to view a Python script, which has its compression algorithm implementation, and run the technical description for details. First fragment of memory dump contains compressed payload, trim the null byte, use this Python script extracted successfully. Resulting file analysis with IDA, is in fact not complete and does not contain a valid import table (import table).
After you decrypt the payload, unpacker creates the file C:\PROGRA~2\Z (c:\ProgramData\Z), the file Kernel32. GetFileType to verification, check for FILE_TYPE_CHAR. If it were, in the case of execute malicious payload, the code ends. Subsequently, the current time, file name, and \r\n, writing to the z files. That looks like the following:
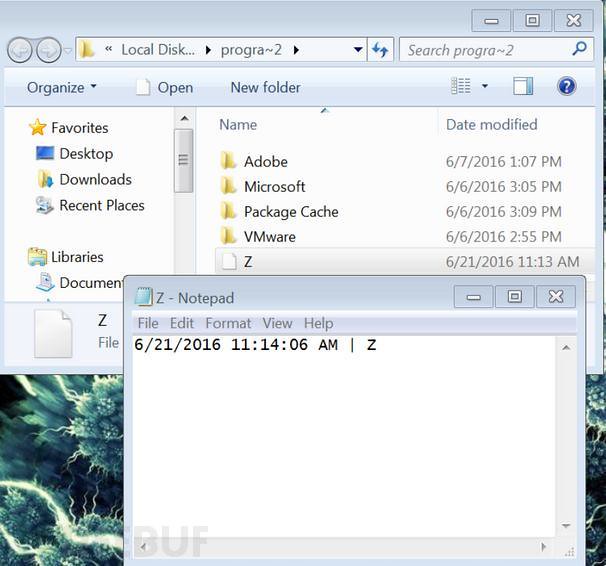
Shortly after the write strings to a file, the file will be deleted. Not sure why you want to do may be to interfere in the analysis process.
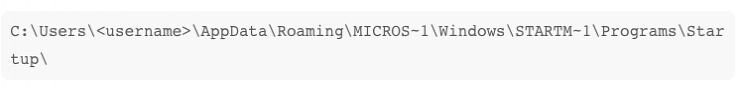
Unpaker queries the registry to confirm that the Startup location:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Startup

C:\Users\ \AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup (Win7 context path)
The role of this position is very clear, Unpack the code inside HTML blackmail letters focused on the process of this is extortion.
From the analysis of the sample, from a. Ink the shortcuts perform, the shortcut Rundll32.exe F0F3.tmp.dll,MSX3. Here, behind the MSX3 is an additional parameter, this command F0F3.tmp.dll is loaded, subsequent MSX3 function. MSX3 function unpacker does not actually exist, so it must be part of the payload.
So there is likely to be dumped by calling the VirtualProtect unpack after the payload. Since it requires the MSX3 the address of the function, I set a breakpoint in GetProcAddress.
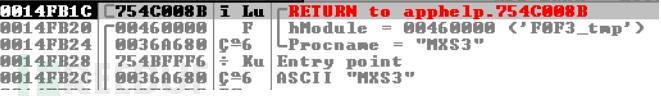
MSX3 address back, execution jumps to the address, file encryption, blackmail begins.
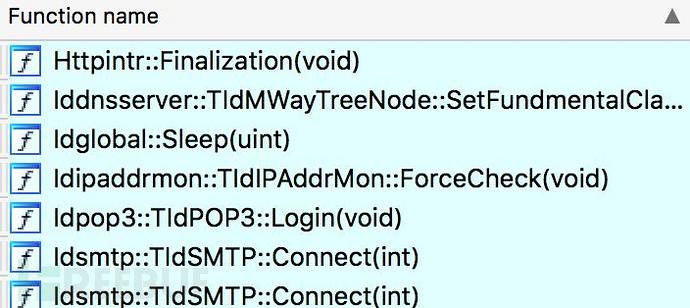
Seems to be payload compiled with Delphi, known from the following information. From the list below, some imports seem to be using DNS, POP3, and SMTP protocols. But these functions compared to MSX3, should be invoked by a different entry point.
Eventually, Ransomware locked files using RSA and RC4 encryption, encryption file extension after. cryp1, previous versions of the extension. crypt. As mentioned earlier, the previous version can decrypt the decryption tool, but the new version will not be achieved.
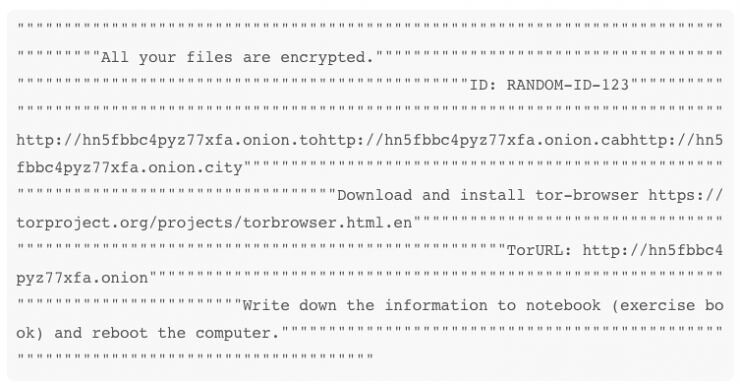
Inside each folder that contains the file that is encrypted with extortion. One is a text file, another is the HTML format. Text forms of extortion are the following:
As mentioned earlier a new version CryptXXX added new feature: file encryption, backup of all files on the disk will be deleted, prevents users from using a file recovery this trick.
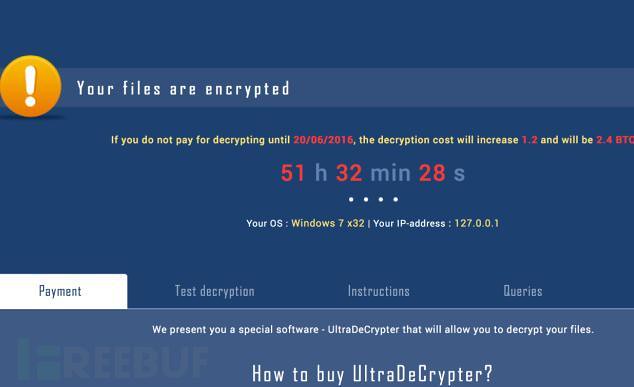
Blackmail information is displayed on the screen looks like this:
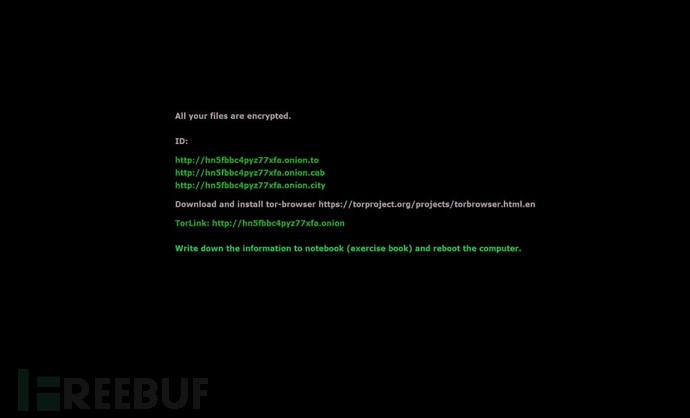
In order to alert the user that the seriousness of the problem, CryptXXX
Path, created .html and .bmp files. Also blackmail, but mentioned above are slightly different, and will appear after you restart the computer:
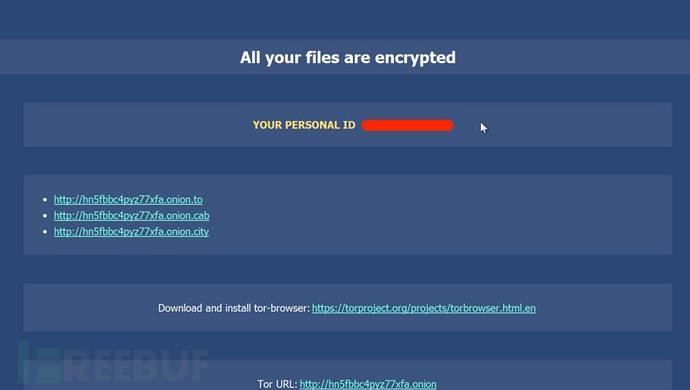
Takes you to the payment page, the page will be for victims to fill out the appropriate information, Ransomware is assigned ID:
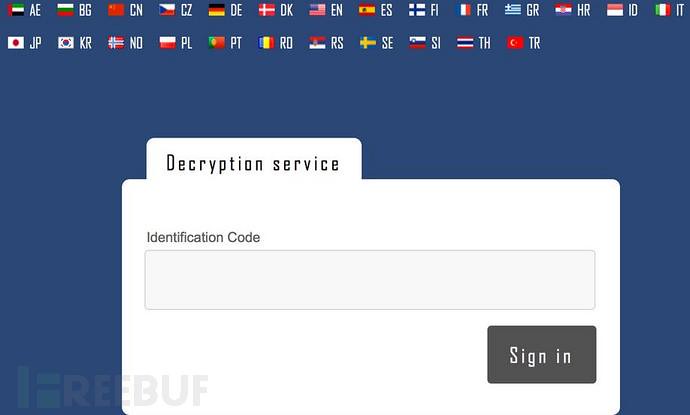
After you log in with the ID, the following page is displayed:
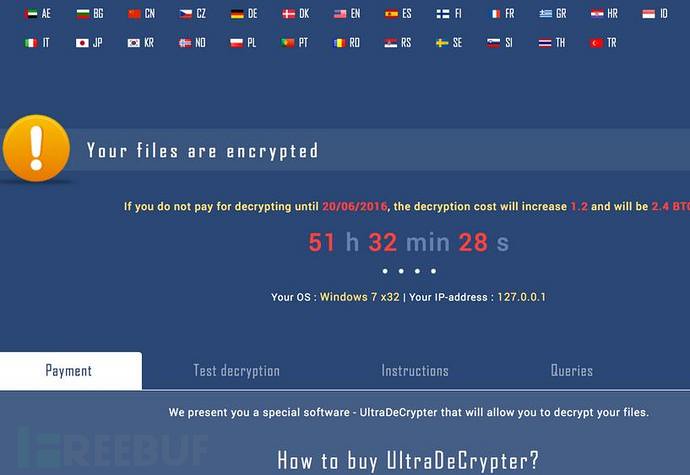
If victims have never heard of coins, or will not be paid for with coins, so it does not matter, this page will teach you how to do the following.
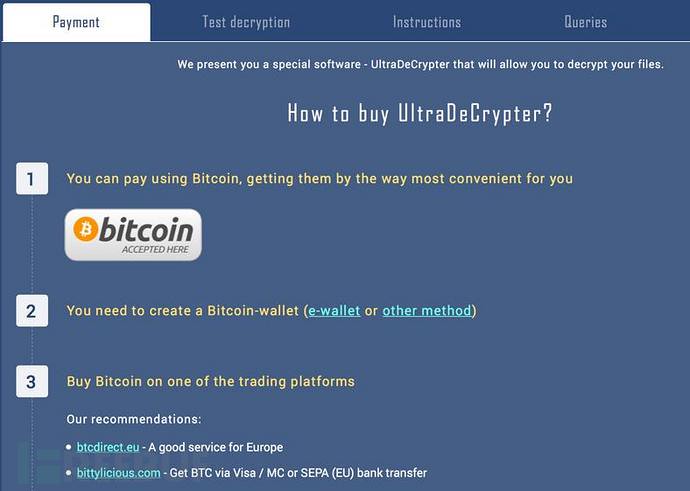
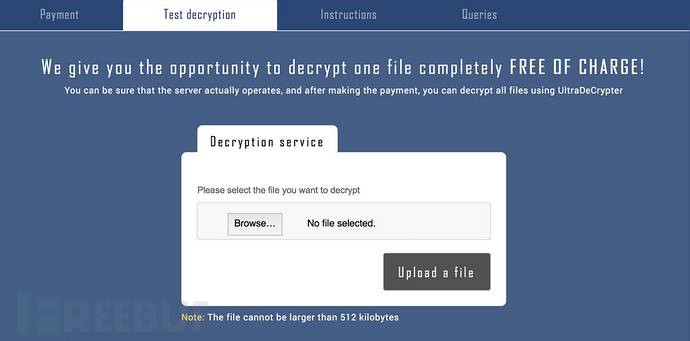
In order to prove that they are indeed provide a decryption services, this page is primarily intended for decrypting services for victims of the trial (service very close), but this so-called trial service, decrypt the file size limit in 512KB.
Prevent rogue blackmail software recommendations
Ransomware to avoid infection, as well as other malware. Keep the browser and Windows-related components (Java, Adobe, etc) get the latest updates. In addition, to keep the browser clean, attention can lead to infection of malicious adware prevention of intrusion, and don't open unknown email attachments easily. This version of the CryptXXX have the ability to delete shadow volume the disk backup file, then you may actually consider backing up important files to a different location. Jack Spade iPhone 5 Case Jack Spade iPhone 5 Case
Lei Feng network Note: article source: arstechnica, and sentinelone, compiled by the rice ball-June, FreeBuf exclusive article authorized network of Lei Feng (search for "Lei feng's network" public concerns), published, reproduced, please indicate the source (FreeBuf.COM FreeBuf hackers and geeks).